
Oracle Database Test Application
Peter Goldthorp, Dito. February 2022
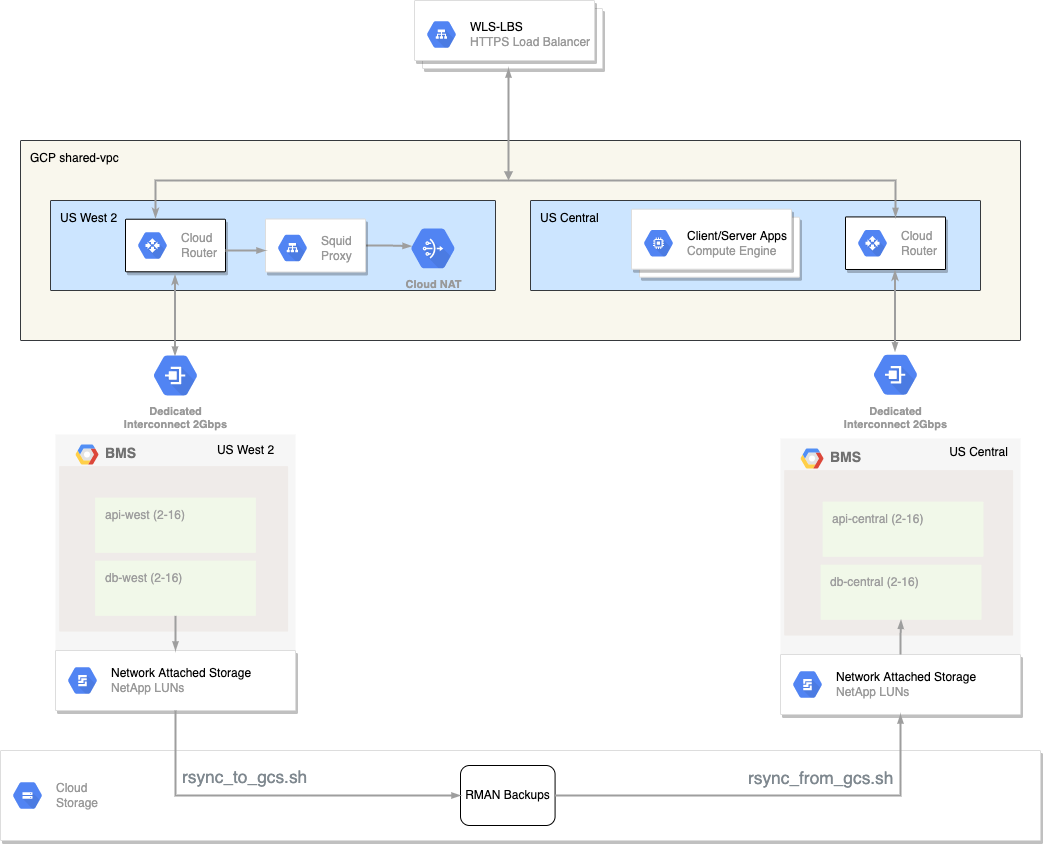
Dummy application to test the configuration of a newly deployed BMS environment prior to starting a migration. It supports testing:
- Network connectivity between the API server and database server on OLVM configured VMs in a BMS deployment
- Network egress via a Squid proxy for API calls from the database server
- Network ingress via a GCP global load balancer to the API server
- Database updates and associated archive log files for testing backup and recovery via GCS
- Client/server network connections from GCP VMs to an Oracle database
- Load balancer configuration to switch traffic between regions
Application Overview
Configures a mini application comprising an Oracle XE database and an application server. The database uses UTL_HTTP to make calls to api.weather.gov and get weather forecasts for a given location. It stores the result in a database table. The API server reads this table and responds to GET requests for weather forecasts.
The application creates a database user called tracker with a stored procedure dito_weather_get that makes calls to api.weather.gov to get weather forecasts for a given location. The results of these api calls are stored in a database table called dito_weather. The dito_weather_get procedure can also be used to test internet egress via the squid_proxy.
Database setup instructions
Create a VM and install an Oracle XE database by following the instructions in the Oracle XE install guide. Note, the download locations in the XE install guide don’t work for OEL8. Use the following instead:
dnf -y install oracle-database-preinstall-21c
wget https://download.oracle.com/otn-pub/otn_software/db-express/oracle-database-xe-21c-1.0-1.ol8.x86_64.rpm
dnf -y localinstall oracle-database-xe-21c-1.0-1.ol8.x86_64.rpm
Edit the .bash_profile file in /home/oracle/
su - oracle
vi .bash_profile
## Append
export ORACLE_HOME=/opt/oracle/product/21c/dbhomeXE
export ORACLE_SID=XE
export PDB_NAME=XEPDB1
export ORAENV_ASK=NO
. /opt/oracle/product/21c/dbhomeXE/bin/oraenv
source .bash_profile
Open port 1521 in firewalld:
sudo -s
firewall-cmd --get-active-zones
firewall-cmd --zone=public --add-port=1521/tcp --permanent
firewall-cmd --reload
App install
Create a wallet
mkdir /home/oracle/wallets
orapki wallet create -wallet /home/oracle/wallets/apiwallet -pwd @DFADlskks
mkdir /home/oracle/certs
vi certs/digicert.pem
-----BEGIN CERTIFICATE-----
MIIElDCCA3ygAwIBAgIQAf2j627KdciIQ4tyS8+8kTANBgkqhkiG9w0BAQsFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0xMzAzMDgxMjAwMDBaFw0yMzAzMDgxMjAwMDBaME0xCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxJzAlBgNVBAMTHkRpZ2lDZXJ0IFNIQTIg
U2VjdXJlIFNlcnZlciBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
ANyuWJBNwcQwFZA1W248ghX1LFy949v/cUP6ZCWA1O4Yok3wZtAKc24RmDYXZK83
nf36QYSvx6+M/hpzTc8zl5CilodTgyu5pnVILR1WN3vaMTIa16yrBvSqXUu3R0bd
KpPDkC55gIDvEwRqFDu1m5K+wgdlTvza/P96rtxcflUxDOg5B6TXvi/TC2rSsd9f
/ld0Uzs1gN2ujkSYs58O09rg1/RrKatEp0tYhG2SS4HD2nOLEpdIkARFdRrdNzGX
kujNVA075ME/OV4uuPNcfhCOhkEAjUVmR7ChZc6gqikJTvOX6+guqw9ypzAO+sf0
/RR3w6RbKFfCs/mC/bdFWJsCAwEAAaOCAVowggFWMBIGA1UdEwEB/wQIMAYBAf8C
AQAwDgYDVR0PAQH/BAQDAgGGMDQGCCsGAQUFBwEBBCgwJjAkBggrBgEFBQcwAYYY
aHR0cDovL29jc3AuZGlnaWNlcnQuY29tMHsGA1UdHwR0MHIwN6A1oDOGMWh0dHA6
Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RDQS5jcmwwN6A1
oDOGMWh0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RD
QS5jcmwwPQYDVR0gBDYwNDAyBgRVHSAAMCowKAYIKwYBBQUHAgEWHGh0dHBzOi8v
d3d3LmRpZ2ljZXJ0LmNvbS9DUFMwHQYDVR0OBBYEFA+AYRyCMWHVLyjnjUY4tCzh
xtniMB8GA1UdIwQYMBaAFAPeUDVW0Uy7ZvCj4hsbw5eyPdFVMA0GCSqGSIb3DQEB
CwUAA4IBAQAjPt9L0jFCpbZ+QlwaRMxp0Wi0XUvgBCFsS+JtzLHgl4+mUwnNqipl
5TlPHoOlblyYoiQm5vuh7ZPHLgLGTUq/sELfeNqzqPlt/yGFUzZgTHbO7Djc1lGA
8MXW5dRNJ2Srm8c+cftIl7gzbckTB+6WohsYFfZcTEDts8Ls/3HB40f/1LkAtDdC
2iDJ6m6K7hQGrn2iWZiIqBtvLfTyyRRfJs8sjX7tN8Cp1Tm5gr8ZDOo0rwAhaPit
c+LJMto4JQtV05od8GiG7S5BNO98pVAdvzr508EIDObtHopYJeS4d60tbvVS3bR0
j6tJLp07kzQoH3jOlOrHvdPJbRzeXDLz
-----END CERTIFICATE-----
** (see openssl command below) **
orapki wallet add -wallet /home/oracle/wallets/apiwallet -trusted_cert -cert /home/oracle/certs/digicert.pem
orapki wallet display -wallet /home/oracle/wallets/apiwallet/
Edit the acl.sql script. Uncomment and edit the proxy server entry. Example:
BEGIN
DBMS_NETWORK_ACL_ADMIN.ASSIGN_ACL (
acl => 'api-acl.xml',
host => 'squid-proxy.my.domain.com',
lower_port => 3128,
upper_port => 3128);
COMMIT;
END;
/
Login to SQL*Plus as system@localhost:1521/xepdb1 and run create_user.sql and acl.sql
Connect as tracker and run dito_weather.sql and dito_weather_proc.sql
Run procedure
Edit the get_weather_forecast.sh shell script to include the proxy server details. Example:
#!/bin/bash
# Edit or remove the proxy argument as required
source /home/oracle/.bash_profile
/opt/oracle/product/21c/dbhomeXE/bin/sqlplus tracker/tracker@localhost:1521/xepdb1 <<ENDOFSQL
exec dito_weather_get('file:/home/oracle/wallets/apiwallet','@DFADlskks',
'Mims, Florida','MLB/45,76','squid-proxy.my.domain.com:3128')
exec dito_weather_get('file:/home/oracle/wallets/apiwallet','@DFADlskks',
'Salt Lake City, Utah','SLC/99,174','squid-proxy.my.domain.com:3128')
exec dito_weather_get('file:/home/oracle/wallets/apiwallet','@DFADlskks',
'Los Angeles, California','LOX/154,44','squid-proxy.my.domain.com:3128')
exec dito_weather_get('file:/home/oracle/wallets/apiwallet','@DFADlskks',
'Council Bluffs, Iowa','OAX/84,59','squid-proxy.my.domain.com:3128')
exit;
ENDOFSQL
Use it to execute api calls. For example, the following crontab will execute every hour.
0 * * * * /home/oracle/cron/get_weather_forecast.sh
Turn on Archive Logging
The newly installed XE database will be running in No Archive Mode. Login to SQL*Plus as oracle and turn archive logging on
sqlplus / as sysdba
SQL> archive log list
Database log mode No Archive Mode
Automatic archival Disabled
Archive destination /opt/oracle/homes/OraDBHome21cXE/dbs/arch
Oldest online log sequence 3
Current log sequence 5
SQL> shutdown immediate
Database closed.
Database dismounted.
ORACLE instance shut down.
SQL> startup mount
ORACLE instance started.
Total System Global Area 1157625952 bytes
Fixed Size 9685088 bytes
Variable Size 402653184 bytes
Database Buffers 738197504 bytes
Redo Buffers 7090176 bytes
Database mounted.
SQL> alter database archivelog;
Database altered.
SQL> alter database open;
Database altered.
SQL> archive log list
Database log mode Archive Mode
Automatic archival Enabled
Archive destination /opt/oracle/homes/OraDBHome21cXE/dbs/arch
Oldest online log sequence 3
Next log sequence to archive 5
Current log sequence 5
API Server setup
The API server creates a Node JS Express instance that connects to the database using node-oracledb. It should be installed on a separate VM to the database server.
-
Follow instructions in Node.js on Oracle Linux to install Node on the VM
yum install -y oracle-nodejs-release-el7 oracle-release-el7 yum install nodejs - Download and install the latest
oracle-instantclient-basicandoracle-instantclient-sqlplusrpm files from the Oracle Instant Client repo- Tip: use yum to install wget and then edit /etc/wgetrc to specify the proxy location
- Use yum to install the rpm file. Example:
yum localinstall oracle-instantclient-basic-21.5.0.0.0-1.x86_64.rpm yum localinstall oracle-instantclient-sqlplus-21.5.0.0.0-1.x86_64.rpm yum install node-oracledb-node16 - Copy the contents of the api-server directory to an empty directory
- Edit the checkConnections.js and index.js files to include database connection details
-
Run
npm installnpm config set proxy http://squid-proxy:3128 npm install - Run
node checkConnections.jsto verify connections between the VM and the database - Run
node index.jsto start the API server- The APi server process will start on port 3000
curl localhost:3000/forecaststo see results- Open http://host-ip-address:3000 in a browser to see result in a web page
- open a ingress firewall rule for port 3000 to test connections from GCP
sudo firewall-cmd --zone=public --add-port=3000/tcp --permanent sudo firewall-cmd --reload
Get certificate chain
The following code block shows and example of how to find the a certificate for inclusion in a wallet file.
openssl s_client -connect api.weather.gov:443 -showcerts
CONNECTED(00000005)
depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
verify return:1
depth=1 C = US, O = DigiCert Inc, CN = DigiCert SHA2 Secure Server CA
verify return:1
depth=0 C = US, ST = Maryland, L = College Park, O = National Oceanic and Atmospheric Administration, CN = weather.gov
verify return:1
---
Certificate chain
0 s:/C=US/ST=Maryland/L=College Park/O=National Oceanic and Atmospheric Administration/CN=weather.gov
i:/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA
-----BEGIN CERTIFICATE-----
MIIM0TCCC7mgAwIBAgIQAsbN/R+nPcwEXceLmHohjjANBgkqhkiG9w0BAQsFADBN
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMScwJQYDVQQDEx5E
aWdpQ2VydCBTSEEyIFNlY3VyZSBTZXJ2ZXIgQ0EwHhcNMjExMjA2MDAwMDAwWhcN
MjIwODE4MjM1OTU5WjCBhzELMAkGA1UEBhMCVVMxETAPBgNVBAgTCE1hcnlsYW5k
MRUwEwYDVQQHEwxDb2xsZWdlIFBhcmsxODA2BgNVBAoTL05hdGlvbmFsIE9jZWFu
aWMgYW5kIEF0bW9zcGhlcmljIEFkbWluaXN0cmF0aW9uMRQwEgYDVQQDEwt3ZWF0
aGVyLmdvdjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMnxFLgVY2r4
PFuoDb6ohDlPe+3fnycEqhEFc1BY3SC0ke3mO1DH0VhrWn8Go9y5tURNsjG0pu7r
7FhEm209quu+AG0dtlqBqlAbS61iYURQaWbYVM+hqFqxLpD/EhU9DvgGp9bXaeQ0
8sq4e99lEc4FbD7/lpdX6j5+djbZWPJTOE6BeCUso8zB5ZLVslIMyWmtU83T94BX
TJrT4DbFDPAaYywmhZBJFjR7OOKjhGbnxhBkLCo+gQqsBnuYj4Sl8XrBNelTNVxH
hHlDVH+DwkmUXaenGL6MxVtrzJoh7cn9v/q0x1a6b5Uj16KS1eRON6MfyVnRFovD
pXTB06+bR50CAwEAAaOCCXAwgglsMB8GA1UdIwQYMBaAFA+AYRyCMWHVLyjnjUY4
tCzhxtniMB0GA1UdDgQWBBS5plsSACdR+z6XCk49xxqkN8ASdzCCBjoGA1UdEQSC
BjEwggYtghF3d3d4LndyaC5ub2FhLmdvdoIQd3d3LndyaC5ub2FhLmdvdoIPd3d3
LndlYXRoZXIuZ292ghV3d3cudnd0Lm5jZXAubm9hYS5nb3aCFHd3dy50c3VuYW1p
Lm5vYWEuZ292gg93d3cudHN1bmFtaS5nb3aCEHd3dy5zcmgubm9hYS5nb3aCGHd3
dy5yaXBjdXJyZW50cy5ub2FhLmdvdoIQd3d3LnByaC5ub2FhLmdvdoIWd3d3Lm9w
YWgubmNlcC5ub2FhLmdvdoIQd3d3Lm53cy5ub2FhLmdvdoIVd3d3Lm5vd2NvYXN0
Lm5vYWEuZ292ghZ3d3cubmRzYy5uY2VwLm5vYWEuZ292ghV3d3cubmNvLm5jZXAu
bm9hYS5nb3aCEXd3dy5uY2VwLm5vYWEuZ292ghV3d3cubGliLm5jZXAubm9hYS5n
b3aCGXd3dy5jcGNwYXJhLm5jZXAubm9hYS5nb3aCF3d3dy5hdmlhdGlvbndlYXRo
ZXIuZ292ggt3ZWF0aGVyLmdvdoIRd2F0ZXIud2VhdGhlci5nb3aCDncyLndlYXRo
ZXIuZ292gg53MS53ZWF0aGVyLmdvdoILdHN1bmFtaS5nb3aCGXRlc3Qtbm9tYWRz
Lm5jZXAubm9hYS5nb3aCEHNzZC53cmgubm9hYS5nb3aCEnJzbWMubmNlcC5ub2Fh
LmdvdoIUcmlwY3VycmVudHMubm9hYS5nb3aCF3JhZGFyM3B1Yi5uY2VwLm5vYWEu
Z292ghdyYWRhcjJwdWIubmNlcC5ub2FhLmdvdoIRcmFkYXIud2VhdGhlci5nb3aC
FHJhZGFyLXYyLndlYXRoZXIuZ292ghRyYTQtZ2lmcy53ZWF0aGVyLmdvdoIQcHR3
Yy53ZWF0aGVyLmdvdoIUcHJvZHVjdHMud2VhdGhlci5nb3aCE3ByZXZpZXcud2Vh
dGhlci5nb3aCGXByZXZpZXctcmFkYXIud2VhdGhlci5nb3aCHXByZXZpZXctb3Bl
bmdlby5uY2VwLm5vYWEuZ292ghxwcmV2aWV3LWlkcGdpcy5uY2VwLm5vYWEuZ292
gh9wcmV2aWV3LWZvcmVjYXN0LXYzLndlYXRoZXIuZ292ghdwcmV2aWV3LWFwaS53
ZWF0aGVyLmdvdoIacHJldmlldy1hbGVydHMud2VhdGhlci5nb3aCFW9wZW5nZW8u
bmNlcC5ub2FhLmdvdoIPbndzLndlYXRoZXIuZ292ghFub3djb2FzdC5ub2FhLmdv
doIWbm93Y29hc3QubmNlcC5ub2FhLmdvdoISbm9tYWRzLndlYXRoZXIuZ292ghRu
b21hZHMubmNlcC5ub2FhLmdvdoIVbmV3Lm5vd2NvYXN0Lm5vYWEuZ292ghJtb2Jp
bGUud2VhdGhlci5nb3aCEm1hcmluZS53ZWF0aGVyLmdvdoIVbWFncGFyYS5uY2Vw
Lm5vYWEuZ292ghFtYWcubmNlcC5ub2FhLmdvdoITbWFkaXMubmNlcC5ub2FhLmdv
doIYbWFkaXMtZGF0YS5uY2VwLm5vYWEuZ292ghJpcmlzLm5jZXAubm9hYS5nb3aC
Emlud3MubmNlcC5ub2FhLmdvdoIUaWRwZ2lzLm5jZXAubm9hYS5nb3aCFWh5c3Bs
aXQubmNlcC5ub2FhLmdvdoISaGFkcy5uY2VwLm5vYWEuZ292ghVncmFwaGljYWwu
d2VhdGhlci5nb3aCHWdpc2Mtd2FzaGluZ3Rvbi5uY2VwLm5vYWEuZ292ghRmb3Jl
Y2FzdC53ZWF0aGVyLmdvdoIXZm9yZWNhc3QtdjMud2VhdGhlci5nb3aCDmYxLndl
YXRoZXIuZ292ghNkaWdpdGFsLndlYXRoZXIuZ292ghFjZnMubmNlcC5ub2FhLmdv
doITYXZpYXRpb253ZWF0aGVyLmdvdoIPYXBpLndlYXRoZXIuZ292ghJhcGktdjEu
d2VhdGhlci5nb3aCE2FtZGFyLm5jZXAubm9hYS5nb3aCEmFsZXJ0cy53ZWF0aGVy
LmdvdoIVYWxlcnRzLXYyLndlYXRoZXIuZ292ghZhaXJxdWFsaXR5LndlYXRoZXIu
Z292MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUH
AwIwbwYDVR0fBGgwZjAxoC+gLYYraHR0cDovL2NybDMuZGlnaWNlcnQuY29tL3Nz
Y2Etc2hhMi1nNi0xLmNybDAxoC+gLYYraHR0cDovL2NybDQuZGlnaWNlcnQuY29t
L3NzY2Etc2hhMi1nNi0xLmNybDA+BgNVHSAENzA1MDMGBmeBDAECAjApMCcGCCsG
AQUFBwIBFhtodHRwOi8vd3d3LmRpZ2ljZXJ0LmNvbS9DUFMwfAYIKwYBBQUHAQEE
cDBuMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wRgYIKwYB
BQUHMAKGOmh0dHA6Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydFNIQTJT
ZWN1cmVTZXJ2ZXJDQS5jcnQwDAYDVR0TAQH/BAIwADCCAX4GCisGAQQB1nkCBAIE
ggFuBIIBagFoAHcAKXm+8J45OSHwVnOfY6V35b5XfZxgCvj5TV0mXCVdx4QAAAF9
kU5P2QAABAMASDBGAiEA23Pv9ioNxKUXR5opobPiutAhFG6Z9HFpTQ4jgfrgsD0C
IQCX7qvDrzC8i6Q4zfy9CsmYTLY1KFLL5QZAanlC+wHOpwB2AFGjsPX9AXmcVm24
N3iPDKR6zBsny/eeiEKaDf7UiwXlAAABfZFOT+oAAAQDAEcwRQIhAPWCu8pvXe+U
JBSQrIwhrOCzkxCrKk36O5N9f/OxAebHAiButXMvxqhhaYcoSBJ61FaR7RFFrdfb
4uP+ZQcGbIewqAB1AEHIyrHfIkZKEMahOglCh15OMYsbA+vrS8do8JBilgb2AAAB
fZFOT6UAAAQDAEYwRAIgZRt5RnQuOvN2frCjyrBBGlpLaiV9nC02GHDvnxJPLdMC
IEBhvCLsrOR2ulBSGt9q7Bx0qvG2PwB/DwIf/EQY7Tk3MA0GCSqGSIb3DQEBCwUA
A4IBAQCrg58KQaOBvH2xHfwe82VdG1caNywHNb129ki555drNCnGbG7BgkR9raWL
/1UjMh5N+ycnjk9yKszQrxNEGu+5MTIN3kpWx18RMNS3T8YusSFmW1zFNfM3HksS
ot7t77z+TmBEUu++ROW9PsE0qfSXb0chiVgLiRSDRspGl04f3sgdktdt2JrLof5N
bwOu1EFGCwA7TrM1J/OvRSRKvwluvcgBS3vhKnmI20IZEskYUSU8hgaFd14hPSOv
4bYBPkDQhQgJeRuLPfJR6O+ohZ3G/dKlebJK4iyH77KYpACl69zONuKOQ8jVzW+0
tcvIru2Uiy2Eyjbg7tX+M0rgmlUL
-----END CERTIFICATE-----
1 s:/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA
i:/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA
-----BEGIN CERTIFICATE-----
MIIElDCCA3ygAwIBAgIQAf2j627KdciIQ4tyS8+8kTANBgkqhkiG9w0BAQsFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0xMzAzMDgxMjAwMDBaFw0yMzAzMDgxMjAwMDBaME0xCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxJzAlBgNVBAMTHkRpZ2lDZXJ0IFNIQTIg
U2VjdXJlIFNlcnZlciBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
ANyuWJBNwcQwFZA1W248ghX1LFy949v/cUP6ZCWA1O4Yok3wZtAKc24RmDYXZK83
nf36QYSvx6+M/hpzTc8zl5CilodTgyu5pnVILR1WN3vaMTIa16yrBvSqXUu3R0bd
KpPDkC55gIDvEwRqFDu1m5K+wgdlTvza/P96rtxcflUxDOg5B6TXvi/TC2rSsd9f
/ld0Uzs1gN2ujkSYs58O09rg1/RrKatEp0tYhG2SS4HD2nOLEpdIkARFdRrdNzGX
kujNVA075ME/OV4uuPNcfhCOhkEAjUVmR7ChZc6gqikJTvOX6+guqw9ypzAO+sf0
/RR3w6RbKFfCs/mC/bdFWJsCAwEAAaOCAVowggFWMBIGA1UdEwEB/wQIMAYBAf8C
AQAwDgYDVR0PAQH/BAQDAgGGMDQGCCsGAQUFBwEBBCgwJjAkBggrBgEFBQcwAYYY
aHR0cDovL29jc3AuZGlnaWNlcnQuY29tMHsGA1UdHwR0MHIwN6A1oDOGMWh0dHA6
Ly9jcmwzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RDQS5jcmwwN6A1
oDOGMWh0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RD
QS5jcmwwPQYDVR0gBDYwNDAyBgRVHSAAMCowKAYIKwYBBQUHAgEWHGh0dHBzOi8v
d3d3LmRpZ2ljZXJ0LmNvbS9DUFMwHQYDVR0OBBYEFA+AYRyCMWHVLyjnjUY4tCzh
xtniMB8GA1UdIwQYMBaAFAPeUDVW0Uy7ZvCj4hsbw5eyPdFVMA0GCSqGSIb3DQEB
CwUAA4IBAQAjPt9L0jFCpbZ+QlwaRMxp0Wi0XUvgBCFsS+JtzLHgl4+mUwnNqipl
5TlPHoOlblyYoiQm5vuh7ZPHLgLGTUq/sELfeNqzqPlt/yGFUzZgTHbO7Djc1lGA
8MXW5dRNJ2Srm8c+cftIl7gzbckTB+6WohsYFfZcTEDts8Ls/3HB40f/1LkAtDdC
2iDJ6m6K7hQGrn2iWZiIqBtvLfTyyRRfJs8sjX7tN8Cp1Tm5gr8ZDOo0rwAhaPit
c+LJMto4JQtV05od8GiG7S5BNO98pVAdvzr508EIDObtHopYJeS4d60tbvVS3bR0
j6tJLp07kzQoH3jOlOrHvdPJbRzeXDLz
-----END CERTIFICATE-----
---
Server certificate
subject=/C=US/ST=Maryland/L=College Park/O=National Oceanic and Atmospheric Administration/CN=weather.gov
issuer=/C=US/O=DigiCert Inc/CN=DigiCert SHA2 Secure Server CA
---
No client certificate CA names sent
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 5118 bytes and written 322 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: FBDD58321626E0865EC9E5D1BACD61EC465735FDE76B7883BDA249072A347212
Session-ID-ctx:
Master-Key: C842C978988F67C6CDF2120647B3930B074C7A0E014EA243D1DC34DBABFCD1925E3EA7289BE767D84A7F640420932811
TLS session ticket lifetime hint: 83100 (seconds)
TLS session ticket:
0000 - 00 00 01 16 ff 68 ce d2-90 11 7c a3 ca e3 17 e8 .....h....|.....
0010 - 58 3e e6 6d 99 e4 58 6b-63 de 8e 84 3e f3 d1 b8 X>.m..Xkc...>...
0020 - b8 e6 75 8f 8a c6 5c ff-1a 98 11 46 6b fb 46 8b ..u...\....Fk.F.
0030 - 44 97 9e a4 84 62 8f 37-0a 01 3a a2 7f 64 c2 f4 D....b.7..:..d..
0040 - b5 18 c2 26 d1 46 a5 48-f6 b6 6b 1a c0 6a 89 bc ...&.F.H..k..j..
0050 - da fe 3f 67 e4 97 06 e4-73 2a 87 1b 5f 61 43 ee ..?g....s*.._aC.
0060 - 31 c7 e9 3c e7 a4 a5 d0-ad ce ea 5b e1 5a 19 ff 1..<.......[.Z..
0070 - 91 ad c9 0d e2 bd 3f 7e-4d 95 77 f6 9b 1d 2d e0 ......?~M.w...-.
0080 - cf 3a 00 5a e6 1a ef 10-27 b4 6f b2 8e 3b b6 4a .:.Z....'.o..;.J
0090 - 90 2f f6 aa 58 6e 6c c9-9b 39 5f 88 c7 22 b2 71 ./..Xnl..9_..".q
Start Time: 1642702252
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
closed
Copyright © Dito LLC, 2023